Combatting Freight Fraud: Identifying Risks and Strategies to Protect Your Business
Freight/Shipping Trends | Agency Ownership | Business Advice | Logistics | Hostage Load | Transportation | Best Practices | Agent Program | Safety | Freight Management
Now that we've explored the types and trends of freight fraud in our previous post, let's focus on the anatomy of a scam and how to spot the red flags. This second part of our series will guide you through the stages of freight fraud, highlight the industries most at risk, and offer strategies to fortify your defense against these threats.
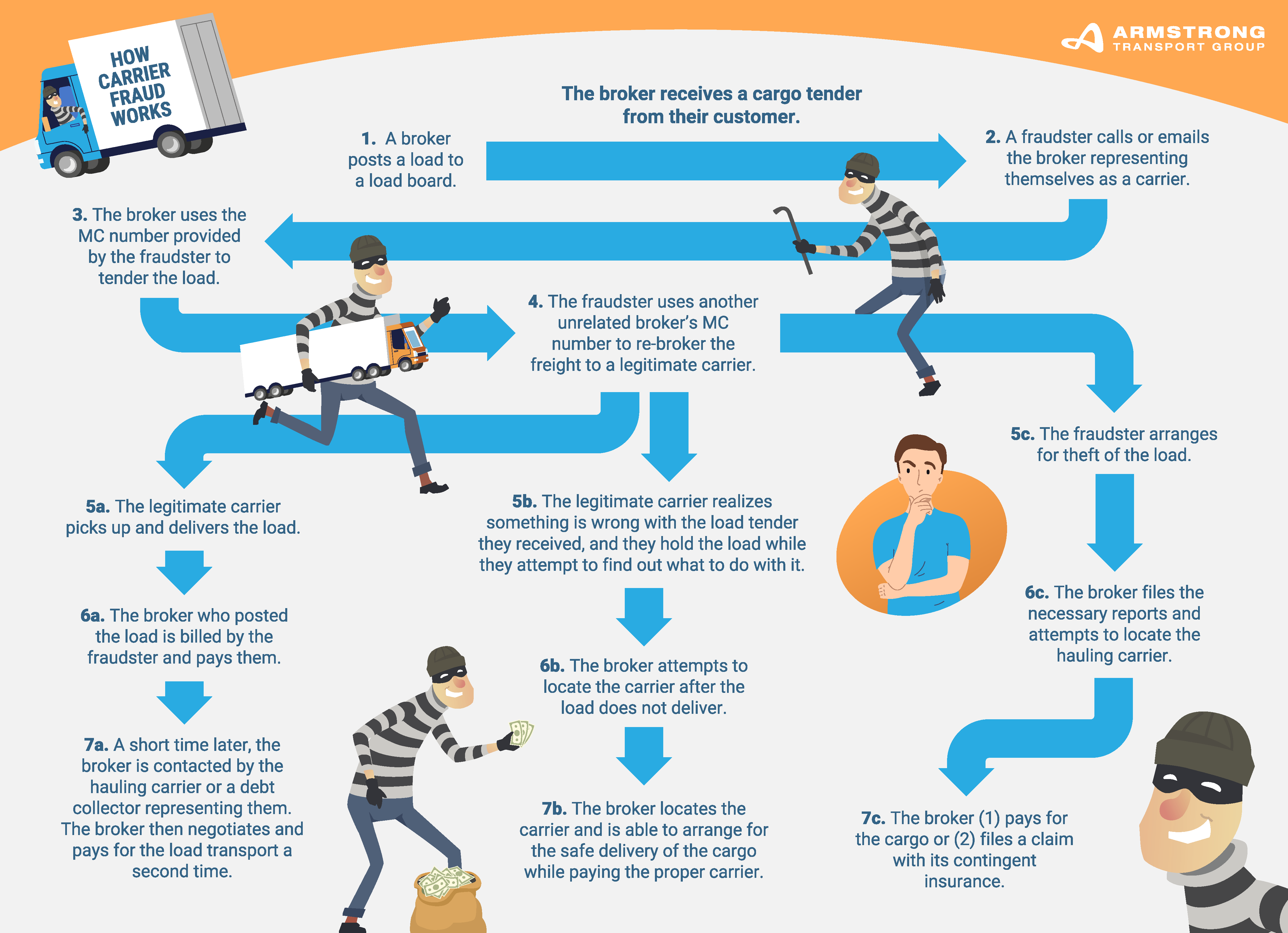
Join us as we continue to explore practical ways to safeguard your business!
The Anatomy of a Scam: How Freight Fraud Happens
Freight fraud can be a complex and orchestrated scam involving several stages. By dissecting the anatomy of a typical scam, businesses can be better prepared to recognize and prevent fraudulent activities.
Stage 1: Targeting and Research
Fraudsters begin by identifying a target, which could be a shipment, a logistics company, or a supply chain process. They conduct thorough research, often using social engineering and information-gathering techniques to understand their target's vulnerabilities.
- Information Gathering: Scammers may use phishing emails to gain access to internal communications, study business practices, or even intercept legitimate emails to understand shipment schedules and routes.
- Identifying Weaknesses: They look for weak spots in security protocols, such as single-factor authentication, unencrypted data transmissions, or employees susceptible to social engineering.
Stage 2: Planning and Setup
With the necessary information in hand, fraudsters move on to planning their scam. This involves creating believable forgeries and setting up the infrastructure needed to carry out the fraud.
- Forging Documents: Scammers often create false identities, counterfeit paperwork, and fictitious companies that appear legitimate to bypass security checks.
- Establishing Communication: They may set up fraudulent email accounts, websites, and phone lines that mimic those of genuine businesses to interact with victims.
Stage 3: Execution
 This is the active phase of the scam, where the fraudsters initiate contact and start the process.
This is the active phase of the scam, where the fraudsters initiate contact and start the process.
- Initial Contact: Using their forged credentials, fraudsters may contact companies as carriers offering their services or as clients seeking transportation for their goods.
- Agreement and Action: Once an agreement is reached, the scammers execute their plan—rerouting shipments, picking up cargo under false pretenses, or initiating fraudulent payments.
Stage 4: Diversion and Theft
In the case of cargo theft, fraudsters will divert shipments to locations they control. In financial fraud, they will redirect payments to their accounts.
- Rerouting Shipments: Fraudsters redirect shipments away from their intended destinations through various tactics like GPS spoofing or falsified instructions.
- Financial Misdirection: By infiltrating payment systems, scammers divert funds through manipulated invoicing or by altering banking details.
Stage 5: Covering Tracks
After the fraud is committed, scammers work to conceal their actions to delay detection and avoid capture.
- Disappearing Act: Fraudulent operators may shut down websites, discard phones, and erase all digital footprints that could lead back to them.
- Document Alteration: They might alter delivery documents or create fake confirmations to make it appear that the transaction was completed successfully.
Understanding how these scams are structured allows businesses to implement strategies to disrupt each stage and reduce the likelihood of falling victim.
The First Line of Defense: Identifying Red Flags
Vigilance is key to combating freight fraud. Recognizing the warning signs early on can help stop a scam in its tracks. Here, we'll detail the red flags businesses should be aware of to thwart fraudulent activities before they can cause harm.
Red Flag #1: Suspicious Communication
- Unsolicited Contact: Be cautious of unsolicited calls, emails, or text messages from new carriers or shippers, especially if they are pushing for urgent action.
- Mismatched Information: Look out for discrepancies between email addresses, phone numbers, and the names or companies they claim to represent.
- Pressure Tactics: High-pressure tactics urging quick decisions or payment can indicate a scam.
Red Flag #2: Anomalies in Documentation
- Inconsistencies in Paperwork: Any discrepancies in documentation, such as the bill of lading, insurance certificates, or carrier paperwork, warrant further investigation.
- Unverifiable Details: Difficulty in verifying the physical address of a company, contact details, their tax ID, or insurance information is a potential warning sign.
Red Flag #3: Too Good to Be True Offers
- Below-market Rates: Offers that come in significantly below market rates can be a lure fraudsters use to entice companies looking for a bargain.
- Guaranteed Capacities: Promises of guaranteed truck capacities during peak times, without credible explanations, should raise suspicions.
 Red Flag #4: Inconsistencies in Business Practices
Red Flag #4: Inconsistencies in Business Practices
- Lack of References: A legitimate company should be able to provide references upon request. Reluctance or inability to do so is concerning.
- Absence of Digital Footprint: A lack of online presence, such as a website or social media activity, could indicate a fly-by-night operation.
Red Flag #5: Transactional Irregularities
- Altered Payment Methods: Requests for changes in established payment methods, such as direct bank transfers instead of through secured payment platforms, may be a sign of fraudulent intent.
- Rush Payments: Demands for rushed payments, especially before services are fully rendered, should warrant caution.
Red Flag #6: Technical Discrepancies
- Website Anomalies: If a company's website lacks functionality, has broken links, or leads to error pages, it may not be legitimate.
- Email Domain Check: Be wary of communications from free email service domains (e.g., @gmail.com or @outlook.com) that may not match the purported company's name.
Implementing Checks and Balances
To combat these risks, companies should:
- Educate Employees: Regular training sessions can keep employees updated on the latest types of fraud and how to recognize them.
- Establish Protocols: Create clear procedures for vetting new contacts and verifying the authenticity of communications and documents.
- Maintain Oversight: Set up an internal system for reporting and investigating red flags.
By being aware of these red flags and implementing a culture of scrutiny and verification, businesses can establish a robust first line of defense against freight fraud.
At the Crossroads: Industries Most at Risk
Certain industries find themselves at a higher risk of freight fraud due to the nature of their goods or the intricacies of their supply chains.
Electronics Industry
- High Value and Demand: Electronic goods are typically high value and in constant demand, making them prime targets for theft and fraud. The small size of items like smartphones and laptops make them particularly attractive for theft and resale on the black market.
- Complex Supply Chains: The electronics supply chain involves multiple transit points and parties, providing numerous opportunities for interception and fraud.
- Case Example: A common scam involves fraudsters posing as legitimate carriers, accepting high-value electronic shipments, and disappearing once the goods are loaded onto their trucks.
Pharmaceuticals and Healthcare
- Sensitive Nature of Goods: Pharmaceuticals require stringent controls and tracking, given their sensitivity and regulatory compliance requirements. The high value and controlled nature of many pharmaceuticals make them a prime target.
- Risks to Public Health: Beyond financial loss, fraudulent activities in this sector pose severe public health risks if counterfeit or stolen drugs reach consumers.
- Case Example: There have been instances where fraudsters have used fake credentials to secure contracts for transporting pharmaceuticals to sell the goods on the black market.
Food and Beverage Industry
 Perishability and Traceability: The perishable nature of food and beverages necessitates swift and reliable transportation, which fraudsters can exploit by promising expedited services to misappropriate goods.
Perishability and Traceability: The perishable nature of food and beverages necessitates swift and reliable transportation, which fraudsters can exploit by promising expedited services to misappropriate goods.- Vulnerability to Pilferage: Partial theft or pilferage is common in this industry, with fraudsters often selling stolen items before the theft is even noticed.
- Case Example: Scammers have been known to hijack refrigerated loads by providing fraudulent temperature records, ensuring the theft goes undetected until delivery.
Apparel and Footwear
- Seasonal Shipments and Returns: The high volume of shipments during seasonal peaks, along with a significant number of returns, provides ample opportunity for fraudsters to infiltrate the supply chain.
- Desirability of Goods: Branded apparel and footwear are highly sought after in the consumer market, making them susceptible to theft and resale.
- Case Example: Cargo theft rings often target shipments during transit, especially those carrying branded items, using insider information to facilitate the crime.
Consumer Packaged Goods (CPG)
- Broad Distribution Networks: The widespread distribution network for CPGs opens multiple avenues for fraudulent activities at various points in the supply chain.
- High Volume and Turnover: The sheer volume of goods moving through the system increases the risk of fraud going unnoticed.
- Case Example: Fraudsters might pose as legitimate retailers placing large orders and then diverting shipments to alternate locations.
Secure Your Future with Armstrong
Freight fraud is a year-round concern costing the industry dearly, and it's only getting more challenging. At Armstrong, we're tackling the problem head-on. Investing in tools like Highway and SaferWatch, we're putting technology at the forefront of our operations to shield our agent partners and their customers from scams like those described above.
If you want to grow your business in 2024 and leverage a brokerage partner who's serious about your security, visit our website and connect with our Agent Success team. Let's work together to keep your network safe while driving your business forward.
About Stephanie Wilson
With over 20 years of experience, Stephanie handles the intake and administration of cargo claims while also resolving emergencies such as hostage loads. As Armstrong's Claims Manager, Stephanie is also responsible for streamlining the department and fostering transparency in the claims process.




