4 Best Practices for Enhancing Digital Security
Agency Ownership | Business Advice | Technology | Logistics | Transportation | Best Practices | Safety | Shippers
With the Russia-Ukraine conflict ongoing and potential cyberattacks looming, it's more important than ever for businesses to remain vigilant against threats. Although larger companies are often the target of cyberattacks, small- and medium-sized organizations are attractive to cybercriminals because they may have fewer resources and security controls to defend against breaches.
Cybercrime is one of the fastest-growing crimes globally, and staying protected may seem difficult with cybercriminals consistently finding new ways to attack. Fortunately, educating yourself on small things that contribute to digital security can go a long way in keeping you and your company protected. In this blog post, we cover tips to enhance IT and email security.
Invest in Security Measures
Data protection may seem like a steep investment for a small business. But it's cheaper (and more effective) to prevent security breaches than to clean one up retroactively. Antivirus and antimalware software, external hard drives to back up data, and secure file-sharing solutions are all integral to enhancing security in your business. Armstrong offers agents free access to Google Workspace, including Google Drive to store and send documents securely!
We recommend regularly checking for updates on your PC/Mac, cell phone, Google Workspace, email client, and any third-party software. Along with adding new features and fixing bugs, developers release updates to enhance security. Installing the latest version of your software keeps you protected against ongoing threats.
Evaluate your hardware annually. Outdated computers and other personal devices may not support new security software and be slower to respond to cyberattacks should they occur. If your laptop is thicker than a 1990s Sears catalog, it may be time to upgrade!

Beware of Phishing
Phishing happens when an attacker impersonates a company or individual to access personal data, like login credentials or credit card numbers, leading to identity theft, funds being re-routed to hackers’ accounts, or ransomware attacks.
Phishers often use email and text messages to transmit malicious links or attachments that can infect your devices. Just one click can enable hackers to infiltrate your company's entire network. A good rule of thumb is to never provide any personal or proprietary information to any communication you didn't request – an unsolicited email, popup webpage, a text message from an unknown number, etc.
Here are some things to look for when identifying potential phishing emails.
Legitimate companies DON’T:
- Request your sensitive information via email. If you receive an unsolicited email from an institution that provides a link or attachment and asks you to provide sensitive information, it’s likely a scam. Most companies will not send you an email asking for passwords, credit card information, credit scores, or tax numbers, nor will they send you a link from which you need to log in.

- Force you to their website. Sometimes phishing emails are coded entirely as a hyperlink. Clicking accidentally or deliberately anywhere in the email will open a fake webpage or download spam onto your computer.
- Send unsolicited attachments. Unsolicited emails that contain attachments reek of hackers. Typically, authentic institutions don't randomly send you emails with attachments but instead direct you to download documents or files on their website.
- Like the tips above, this method isn't foolproof. Sometimes companies that already have your email will send you information, such as a white paper, that may require a download. In that case, be on the lookout for high-risk attachment file types, including .exe, .scr, and .zip. (When in doubt, contact the company directly using contact information obtained from their actual website.)
Legitimate companies DO:
- Typically call you by name. Phishing emails typically use generic salutations such as "Dear valued member," "Dear account holder," or "Dear customer." If a company you deal with required information about your account, the email would call you by name and probably direct you to contact them via phone. But some hackers simply avoid the salutation altogether. This is especially common with advertisements.
- Have domain emails. Don't just check the name of the person sending you the email. Check their email address by hovering your mouse over the 'from' address. Make sure no alterations (like additional numbers or letters) have been made. Just remember, this isn't a foolproof method. Sometimes companies use unique or varied domains to send emails, and some smaller companies use third-party email providers.
- Know how to spell. Possibly the easiest way to recognize a scam email is bad grammar. An email from a legitimate organization should be well-written. Little known fact – there's a purpose behind bad syntax. Hackers generally aren't stupid. They prey on people with less formal education, believing them to be less observant and, thus, easier targets.
Browse the Web Safely
Using a private network is the first step to safely browsing the web. Public networks are full of bad actors looking for data. Be careful connecting to public Wi-Fi hotspots and avoid networks that don't require passwords. There could be a hacker waiting to access your PC via that network.
Private networks are secure because data is encrypted at a packet level, making it hard to steal data out of the air. Use your own network/mobile hotspot through your cell phone provider if possible. These networks use 4G/LTE/5G networks that are relatively safer. We also recommend turning network discovery off or not allowing your device to be seen on the network. Additionally, because you can be hacked via Bluetooth, you should consider turning off your Bluetooth when you're not using it.
Once you are on the Internet, it's important to browse safely. Links can easily be disguised as something they're not. Hovering over a hyperlink can help you determine its legitimacy by showing you the target URL before clicking on it.

The HTTPS protocol is another thing to check for when online. Websites that don't have an SSL certificate cannot guarantee that the transfer of information between you and the site is secure. You can check whether the security certificate is installed by making sure the letters 'HTTPS' (not just 'HTTP') appear before the URL.
If your business has a website, we highly recommend installing this SSL certificate to ensure all information that travels between your server and your visitor's browser is encrypted. (If you don't use HTTPS, visitors will likely see a message at the top of their browser, warning that your site may not be secure.)
Create Strong Passwords and Authentication
Although the temptation to use recycled or generic passwords (123456, anyone?) is strong, they're not secure. If a cybercriminal figures out your password, it could give them access not only to your computer, but to the rest of your company's network.
Complex passwords featuring at least ten characters of uppercase letters, symbols, and numbers are best. Services like LastPass allow you to have super complex passwords that you don't have to remember, though you do need to be connected to Wi-Fi to use it. Additionally, we recommend changing your passwords often (every three to six months).
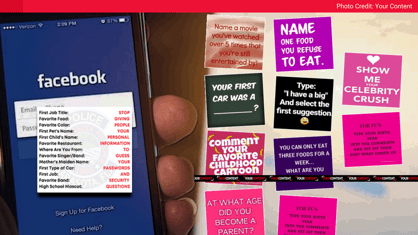 Hackers use social engineering to obtain passwords. Items like kids' birthdays, pets’ names, or your favorite sport make it easier for hackers to guess. Ever been on Facebook and seen a viral post from someone you don't know asking, "Your first car was a: _____?" or "What's your favorite movie of all time?" These question games are often attempts by hackers to access private information, linking your data to a hacker database. Cybercriminals can use that information to figure out passwords and answer security questions.
Hackers use social engineering to obtain passwords. Items like kids' birthdays, pets’ names, or your favorite sport make it easier for hackers to guess. Ever been on Facebook and seen a viral post from someone you don't know asking, "Your first car was a: _____?" or "What's your favorite movie of all time?" These question games are often attempts by hackers to access private information, linking your data to a hacker database. Cybercriminals can use that information to figure out passwords and answer security questions.
Many platforms let you enable two-factor authentication for additional security. This added layer of protection helps ensure that the person accessing the account is really you and not an unauthorized person. We recommend enabling two-factor authentication wherever possible.
Phishing: Reeling It In
No company is immune to cybersecurity threats. Armstrong relies on our employees and agents to be vigilant against phishing to protect our network. Meanwhile, our IT support team works hard to keep Armstrong employees and agents running safely. Looking for an agency partner that’s committed to best-in-class technology and maintaining the security of your office? Connect with our recruiters to find out more about Armstrong’s technology infrastructure.



